This article throws light on how 'Code Injection'
or 'DLL Injection' technique can be used as prominent weapon along
with other techniques to bypass Anti-virus
softwares. It also explains top level technical details revolving
around EXE internals, protectors/packers, encoded shellcodes, inner
working of Antivirus etc
Accompanying this article, you will find video demonstration of 'Injector (POC Tool)' which shows code
injection technique to successfully bypass Antivirus
software on the system.
|
Antivirus (or anti-virus) Software is used to prevent, detect, and
remove, malware, including computer viruses, worms, and Trojan horse.
Such programs may also prevent and remove adware, spyware, and other
forms of malware. Wikipedia
Antivirus play a major role for the
security of a system. But for hackers/ pentesters , it creates some big
problems. During the post exploitation phase we have some sort of excess
on the victim machine and generally we want to upload some tools on the
victim machine for better control but here antivirus play with our tools
and detect them as a malicious file and delete them. Now it may be
possible if you are using your own tool then antivirus may fail to
detect it but this is rare situation during a pentesting. In case, if we
use publicly exposed tools then there is higher probability of getting
caught by antivirus.
A simple example: Suppose we have a reverse
shell now we know that this is a single connection to our machine from
our victim and we dont want to loose it at any condition. So we upload
some tools on the victim machine like netcat or other executable (may be
generated from metasploit) to get a backup connection etc.. may be to
upgrade our shell to merepreter shell. But our victim is using a anti
virus and anti virus delete the uploaded files. Now we need something
else means either bypass AV or write our own code. But the question
here is how antivirus is able to detect our executables (.exe).
|
Basically exe files not only contain your code but also contain some
important data that is only meaningful for a Operating system loader.And technical name for that data is PE (portable executable) file header/ PE
file format. I am not explaining pe file format here. Here is the
snapshot,
PEview - PE File Viewer
Tool :
So when we execute exe, windows loader first read the PE header and
on the basis of header information loader loads the file into memory.br>
Executable Detection (top level view):
So when we
copy the file on system then antivirus scan the file (check for known
signatures) and if the file is malicious then delete the file.
|
The above technologies (Encrypter/packer/protector) are not only to
evade anti viruses. People also use them for ethical work. Basically
encryptor/packers encrypt/pack the file and add the decryption/unpacking
routine into the file. So when we execute the file windows loader loads
the file on the basis of PE header (encryptor/packer does not pack the
PE header of a file they only change the necessary values in PE header.
Eg. Address of entry point, sections etc..). so the unpacking work
something like this:

So unpacking/decryption routine unpack the code and then jump on the
Original Entry Point (on our real code freshly recovered from unpacking
routines).
So if we pack the exe with any packer then Antivirus
should not be able to detect the exe?. Ok now its time to do some
practical.
Pack any malicious file with UPX (a freeware packer) and
then test again with Antivirus. You should see that your AV is again
popping up the alert and telling that hey don't try to fool me it is
malicious.. But our file was packed how AV still know that it is a
malicious file and the answer is AV has also signature for UPX, so what
AV is doing it loads the file detect the packer then decrypt/unpack(AV
also know how to unpack UPX packed files ?) the file and then test the
file, And this is the reason that AV still know that file is malicious.
But hey where is proof that AV is doing all this shit to test file.
Ok to prove just open the same packed file in a hex editor and just
overwrite the starting bytes with some garbage values and then again
test it with your AV. Now you should see that AV is saying that file is
clean (Reason: Because file is corrupted and AV have no option to
unpack/decrypt it) fantastic that's all we want.
|
Because exe files are going to detected by AVs( at least if you pack
them with the publicly exposed packers/encryptors). So we have to think
in a another way.
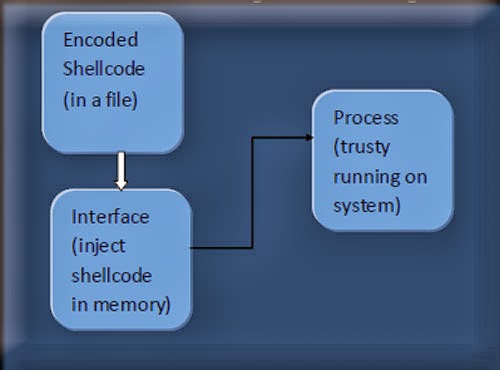
And the another way is: split the exe into two parts
(not
physically)
|
The core code (the actual code that performs a
specific task for eg. Bind shell)
The interface - a mechanism that
will inject the code into memory and execute that code.
|
So the functioning is something like this:
Note that from the above explanation we know that shellcode/code
into a file is not going to be detected by AV because AV dont know how
to decode shellcode. (Dont talk about Heuristic, I know AV vendors are
joking ?)
Important Note: you may be thinking that why I am saying
encoded shellcode because if you use metasploit shellcodes there
signatures may be in AVs. If you encode the shellcode with any available
encoder in metasploit then AVs not able to decode it in a file and not
able to detect it (if you don't understand it read the whole stuff again
?). Although in some cases (Eg. Avast may be with others also) AV not
alert if you use shellcodes that are not encoded because AV think that
txt file are lame files. But if you force fully scan the file than AV
alert.
Second part of the concept is the interface that will inject
the code into a process. Code injection is not a new concept (dll
injection is one of the most popular example).
Note: All the things
are generic and are not specific to any tool or shellcodes. Metasploit
and shellcodes are used only to demonstrate the concept. You can also
inject your codes "that are detectable to AV in exe mode" with this
method and can bypass AV.
|
Things that you can do with this method:
|
Can backdoor a
process
Can provide many backup shells (every type)
|
|
We can use publically available tool (malicious) without fear and
too many other things limited to your wild imaginations.
Video Demonstration:
Here is the video demonstration showing Injection in action
Download Injector:
You can click on below link to download the source code and
executable for the Injector - Proof of Concept code.
|
Author: Amit Malik aka Double_Zer0
|
|
|
|
|










page not found
ReplyDeleteSorry Bro. I will repair the link. Thanks for visiting
Deletevideo link is not there..
ReplyDeleteVideo link is working bro.
DeleteClick on Watch on Viemo link. Wait for 5 seconds then click on SKIP AD button on the upper left corner. ANd you will be redirected to video.
Thanks
I tried and i got 404 Error Page not found. could you [please fix it.
ReplyDeleteBro video link is in working but I am sorry for Injector file it is not available. It is just made for the project and then deleted.
DeleteYou can watch video on this link
http://vimeo.com/14139105